Best Alternatives to Tor Browser
The Tor Project, and their consumer-friendly Tor Browser package, is a great utility for Internet users who are concerned about their online privacy. Though it has been cited as being used for illegal and criminal activities, it isn’t inherently a tool for breaking the law. Rather, it’s based on providing freedom and security for users, to avoid government or other monitoring of Internet traffic, bypass restrictions to browsing, and help keep users’ “identity,” in the form of their IP address, safe and secure.
This is similar, in many ways, to the benefits offered by a VPN service. But, there are significant differences. Here, we’ll take a look at VPNs, proxies, and the Tor Browser, and how they compare and contrast to one another.
VPN Services
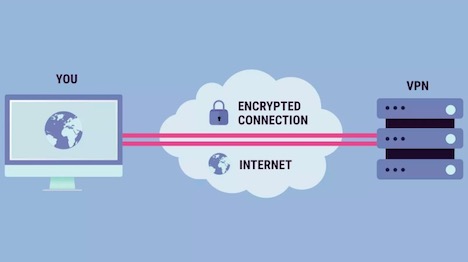
VPN services are perhaps the best-known method today for providing consumers with security, privacy, and anonymity online. These services are usually paid (though some are free), with a monthly or annual subscription typically working out to $5-$10 per month depending on which service you choose. There are over 300 mainstream VPN services around the world today. VPN services encrypt user’s Internet traffic between their machine and their chosen VPN server. At the VPN server, the traffic is decrypted. The server then serves as the origin point for the traffic, using an IP from the VPN server’s pool. Traffic is passed on to the destination server. Then, the process works in reverse for a response from the destination working its way back to the client’s computer.
These services provide security, though the encrypted tunnel between the user and the VPN server. ISPs and government censors or monitors are bypassed – they can’t tell what is in your traffic stream, nor the ultimate destination – merely that you are accessing a VPN server. Your true IP address is protected from being recorded or monitored by destination servers or services, since the only IP address that outside servers see is the one assigned to you by the VPN server. And, because VPN servers from most companies operate in many different countries, you can also use VPN services to bypass geographic restrictions on content.
There are many different VPN providers to choose from, though it can be a bit overwhelming to pick one without additional information. Two of the top providers are NordVPN and Private Internet Access (PIA). A comparison of NordVPN vs. PIA can help highlight the differences between providers, and what they offer in terms of security and privacy options.
Proxy Servers
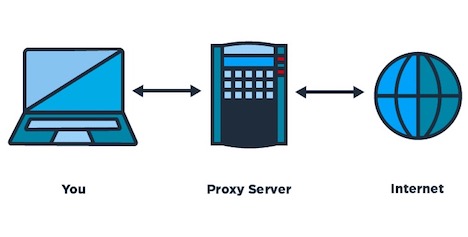
Proxy servers are often free, though sometimes offer paid service options. These servers effectively work to obscure a user’s true IP address when browsing the Internet or using Internet services. Whether they are accessed through a browser interface, or a third-party extension or program, they basically have the same function. User traffic goes to the proxy server, and is then passed on to the destination. The destination servers or services only see the IP of the proxy server. This helps keep the user’s IP hidden, and can be used to bypass geographic content restrictions in some cases too.
However, proxy servers do not offer the same level of security that both VPNs and Tor offer. They do not use encryption, so all traffic is passed “in the clear” and is readable by the government, ISP, or other monitoring entities. At the same time, they are usually not nearly as robust as VPN providers, with less focus on security – they may keep logs, they may be far slower than VPNs or Tor, and may leak or reveal information about users accidentally. They’re a useful tool for getting around IP restrictions, or for a quick, entry-level layer of privacy protection, but don’t hold up to the robust features of Tor and VPNs.
Tor Browser
The Tor Browser bundles the Tor project software with a version of the Mozilla Firefox browser, pre-configured to work on the Tor network. The network consists of a series of relays, run by volunteers and users, that serve as relays. When traffic from a Tor Browser is ready to be sent to a destination server, it first looks at the network for a list of active relays. It encrypts the traffic and all but the first relay IP. Traffic bounces to the first relay, which decrypts the next relay IP, and so forth, until the last relay on the way to the destination. The last relay decrypts the traffic, and passes it to the destination. The process works essentially in reverse for the response traffic.
This means that the destination server only ever sees the IP address of the final relay in the network. What’s more, because the Tor network uses a protocol of randomly choosing relays based on which are active, there’s a great deal of passive security – more than with a VPN service, in fact. Geo-unblocking is also possible, though a bit more work than simply accessing a different server on a VPN. At the same time, the multiple relays and decryption steps mean that browsing with Tor (or using the software for SOCKS or other protocol Internet activities) can be notably slower than with no security in place, and slower than a VPN, which already slows down traffic somewhat. One of the pros for Tor is that the software and network usage are free, whereas the better VPNs are usually paid services. So, there are definitely tradeoffs. Many people prefer Tor Browser for Internet browsing, where speed isn’t a huge consideration, and a VPN for activities like torrenting of video streaming, or bypassing geo-restrictions on content.
A Common Question: Using Tor with a VPN
Many people wonder if you can use the Tor Browser or Tor software with a VPN. In many cases, you can! This adds extra layers of security to your browsing experience, though at the expense of speed (you’ve now got multiple layers of encryption/decryption going on, which takes time). Not all VPNs are set up to work easily with Tor, though most will typically work – just launch the Tor Browser after you’re connected to the VPN. Some of the better providers explicitly provide instructions, or toggles in their client, to fully integrate with the Tor Browser. So, if you’re really worried about security and anonymity, a VPN plus Tor Browser can offer you tremendous security – just at the cost of speed.