How to be Truly Anonymous Online – It’s Harder than You Think
Technology is creating new ways for us to stay connected. But as the internet and smart devices make our lives more convenient than ever before, we also run the risk of losing out on something equally important – our privacy.
Individual privacy is under a constant assault in the age of the internet. With government surveillance, companies tracking our every move while digging for personal data, and cybercriminals out to strip us of our cash, the online world can be a very vulnerable place indeed.
Unfortunately, there is no way to ensure total privacy and anonymity online. Every action we take in the cyber sphere leaves telltale clues that can be traced back to us. But what the internet takes away, it also gives the tools to reclaim it, albeit in a limited way at least. To maintain maximum anonymity online, you will have to use a combination of tools, hardware, safe practices, and above all, a good deal of common sense.
A Secure Operating System
Your privacy starts right from the device which you use to go online – which for most of us is either a PC or more often, a mobile device. Since the mobile device is a whole subject unto itself, let’s start with the computer.
Modern operating systems from companies like Apple and Microsoft can do a lot of cool things, but they are also keeping an eye on your activities. If you value privacy, it is best to look at other options to stay anonymous online.
Linux distros like Tails OS and ZeusGuard are probably the easiest to get into. They have been “endorsed” by government snooping agencies like the NSA as well. Or you can try running special anonymizing operating systems that run on a virtual machine if you are not keen on leaving the comfort of Windows for good.
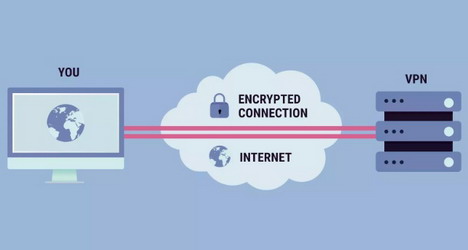
Always Use a VPN
It is not enough that you have a secure OS that doesn’t send your data to its mother ship. On top of that, you also have to ensure that your connection to the cyberspace is not easy to trace. If you are the nomadic type, you can use different public Wi-Fi connections every time you want to go online.
But if you are at a static address with a dedicated internet connection, your next best bet is to use a Virtual Private Network to mask your internet connection. These VPNs replace your IP address with others, sometimes halfway around the world. While free VPNs might do in a pinch, if you are dedicated to staying anonymous, you must invest in a paid service that offers maximum features. There is also the option to buy dedicated hardware designed to protect your online identity.
Browser Options and Search Habits
If you must use your favorite browser like Chrome, Firefox, or Safari, at least make an effort to avoid using browser plug-ins. While they may make life easier with many features and convenience, they also provide chinks in your privacy armor with various security vulnerabilities.
There are exceptions, like the privacy-oriented plug-in called Privacy Badger. It does a host of useful stuff, like stopping ads, preventing sites from tracking you, and even keeping an eye on domains that does shady stuff like place unwanted scripts on any sites you visit.
Another important thing to do is ditch your regular search engine, like Google for instance. They are only interested in selling targeted ads to you, and for that purpose, they keep constant tabs on your online activities.
The best search engine for anonymous browsing has to be Duck Duck Go. They are dedicated to online privacy and do not stand to gain any money from your private data. Granted, they do not offer as many advanced features as Google, but the boost to your privacy is very significant and worth the sacrifice.
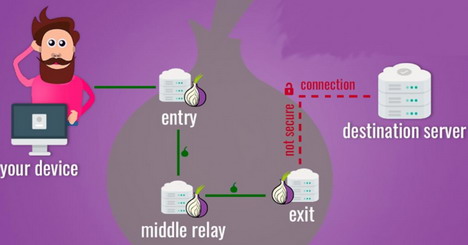
If Possible, Stick with TOR
The Onion Router (TOR) is an entire anonymizing system, made up of an international network of servers, software, API, and a bundled browser that you can install on your PC. It was built initially to help spies and pro-democracy activists in repressive regimes like North Korea to safely contact others online.
TOR has grown in popularity over the years among privacy advocates and generated a fair bit of controversy when it was used by criminals to create black markets online. But regardless of its potential for misuse, TOR still remains a very robust platform for anybody looking to surf the web anonymously.
Use “Burner” Emails
These days, just about every online service asks for your email id. Do not make the mistake of using the same email for all those instances. You will end up getting spammed to oblivion, or worse. Make a habit of creating alternate email IDs that can be disposed of at will, just like temporary burner phones.
If at all possible, stick with special email services that offer maximum privacy. Don’t forget to use anonymizing software like Tor to connect to these emails for an additional layer of security. Do not use the same account more than once if possible, avoid privacy breaches.
Avoid Credit Cards like the Plague
The one thing that can really nail you down in the cyberspace is a money trail that involves traditional institutions like banks and credit cards. It is just as they show in those movies involving fugitives on the run – use your credit card if you want to be tracked and spotted.
Online wallets and money transfer services like Paypal and Skrill are a tad better, but not by much. They can still be tracked easily, and of course, be forced to reveal your info if it is the government doing the tracking.
That leaves us with crypto-currencies as your best bet for any online commerce. Bitcoin and other popular altcoins like Ethereum and Dogecoin are gaining in popularity. They can be used on many online portals to buy stuff.
In fact, there are even online casinos that allow you to wager using crypto-currencies. In these casinos, you don’t have to provide personal details and can just play using your bitcoin wallet or use no deposit casinos. The only weak link in the chain is the moment where you have to use your traditional card or bank account to buy bitcoins from a currency exchange online. But everything you do with it after that is shrouded in privacy.
Avoid Using a Smartphone
This is probably a deal breaker for many folks these days. But there is no escaping the fact – no matter how hard you try it is next to impossible to stop a smartphone from tracking your location and everything you do online. All the data gets stored on the servers of Messrs Google or Apple.
If you must use a phone, stick to disposable prepaid phones or burners. But they still pose a threat as cellphone towers can be used to triangulate your location, not to mention, call records as well.
If you must retain that expensive Android flagship or the latest generation iPhone, there are some temporary fixes that can provide a measure of privacy and anonymity. For starters, you can get apps that allow you to have temporary, anonymous numbers. Linux OS based phones are also an option if you want a smartphone experience without Big Brother watching your every move.
Tags: cyber attack, how to, privacy & security, vpn