Social media – one of several offshoots of the internet – has completely changed the way people interact and socialize in cyber space. With a large number of people spending a good chunk of their time on various social media websites each day; these multimillion dollar corporations have developed huge databases containing personal bio of millions of users. This essentially means that these particular websites, by means of their terms of service, have the liberty to modify, ban or completely remove a user’s content as they see fit.
Tag: privacy & security
How Social Networking Policy is Changing Privacy
How to Protect Your Post Privacy on Facebook
Facebook is the best place for sharing your status updates with family and friends. However, sometimes you might have some interesting outdoor activities which you want to share with your friends only and not your colleagues. Or there are some personal things that can only be shared with your family members and not the others. To manage your post privacy, you should keep these people separated, putting them into groups like family, close friends, colleagues, acquaintances, etc. This helps you to easily share information with relevant people and avoid some sensitive data to be seen by others.
Below we’ve written 2 step-by-step tutorials guiding you to create a friend list of your own on Facebook as well as restrict certain people from seeing your posts. We hope these simple tutorials and screenshots are helpful for protecting your post privacy. Read more…
17 Online Services to Create Strong and Secure Passwords
Password plays a very important security role to prevent any unauthorized access to your computer and online accounts such as Facebook, Gmail and Internet banking accounts.Many people tend to use their own names, date of births, or even a string of easy-to-guess numbers such as 123456 as their passwords. If you use this kind of password, chances are your online accounts are highly vulnerable to hacking. To prevent this happening, we strongly recommend you to check out our previous post titled “40 most hacked passwords you shouldn’t use” to prevent yourself from becoming a victim of cyber criminals.
So, how to create a highly secure but easy to remember password? Below we’ve rounded up a list of online password generators. These free tools enable you to easily create strong and memorable password with just a single mouse click. Most of them allow you to specify password criteria depending on the level of complexity you want. Read more…
5 Best Safety Apps for Kids, Women and Old People
Safety and security are important to everyone regardless of age, gender and place. If you are lost somewhere or encounter violent problems, it’s crucial to identity the issue and call for help immediately.
Below we’ve listed some helpful safety related mobile apps which you can use to call on resources to help you out of the dangerous situation, avoiding you to become a victim of violent crimes such as sexual assault, robbery, etc. These Android and iPhone apps are especially important for kids, women and elderly people. Read more…
Mobile Device Security: A Growing Need in Today’s Expanding BYOD Culture
BYOD: Bring Your Own Device – this phenomena in today’s IT business culture is on the rise and not likely to abate anytime soon. By most measures many IT managers have embraced (at least to some extent, anyway) employee use of their own devices at work for a number of reasons, including saving the company money on expensive hardware expenditures, increasing employee morale, and as one CIO put it, BYOD being “a great way to recruit and retain young talent.”
This paradigm shift seems especially prevalent in IT start-up enterprises. CIOs, managers and other decision makers within these new organizations may be more adept at addressing the phenomena and all it entails provided they are forthright in their assessment and understanding of it. Read more…
Antivirus for Mac: Excess or Necessity?
There’s a wide-spread opinion that the devices that run under Mac OS X are immune to viruses. Do Mac users need to install an antivirus on their devices? In this article I’d like to try and answer this question and also tell you about good antiviruses for Apple devices.
How to Remove Copyright Infringing Web Pages from Google Search Results
Despite the facts that online plagiarism is pretty common in the world of Internet, but as a blogger we will never want to see our hard work being copied and republished on other sites without our consent. If your site is unfortunate, becomes the target of online content thieves, what can you do to deal with them? In the previous posts, we’ve taught you some effective methods for fighting with notorious copycats such as send a warning message, submit a Cease & Desist letter or file a DMCA complaint. Today we’ll show you a quick tutorial guiding you to send a notice of copyright infringement to Google, requesting the search engine to remove copyright infringing webpages from its search results. We hope you’ll find it useful!
How to Stop Facebook Games Requests and Apps Notifications
If you are one of those Facebook users who are sick of receiving game requests such as Diamond Dash and FarmVille from your friends. Here’s a simple tutorial you can follow to get rid of these annoying messages without hurting your friends’ feeling. Apart from blocking game requests, this tutorial can also be used to disable notifications from apps you’ve installed.
23 Free Tools to Check Your Website / Blog’s Security
Nowadays websites are getting more complex, it has never been easy for webmasters and bloggers to ensure their site 100% safe from security threats. Fortunately there are some free web-based tools out there, helping you to scan your site for defects and vulnerabilities.
There is a saying that goes: “prevention is better than cure”, we, as a serious webmaster should regularly monitor the health level of our site and identify any possible security loophole. In today’s post, we’ve gathered 23 really useful web application security tools for website owner like you. Just give them a try and share your experience with us in the comments below. Read more…
6 Ways a Mobile Phone Monitoring Application Can Keep You Safe
In today’s fast-paced world, corporate decisions need to be taken in real time. To support decision making, companies provide their key employees with mobile phones. Working parents are also providing cell phones to their spouses and children. To safeguard against misuse, they install a so-called mobile phone monitoring application on the phones. Perfectly legal to use, this software covertly logs the details of the mobile phone’s activities to the vendor website for secured viewing. This state-of-the-art technology can help you stay safe in more than one way.
8 Easy Tips to Protect Your Facebook Account from Hackers
If Facebook plays an important part in your daily life, you should do whatever necessary to protect your account from being accessed by others without your knowledge. There are many hackers out there actively trying to gain access to our online account for sensitive information and Facebook has always been the hot target for them. In today’s post we would like to share some of the most effective tips to enhance your Facebook security and to protect your privacy so that you won’t be the next victim.
How to Protect Your Gmail Security (10 Best Tips)
As of January 2012, Gmail has 350 million active users worldwide. Due to its popularity, the Google email service has become the target of hackers, phishers and scammers from all over the web. No doubt Gmail has sophisticated security system, but it can never be perfect and 100% invulnerable. As a regular Gmail user, we should do our best to keep our emails, contacts and sensitive information safe. Below we have 10 useful tips which you can use to further strengthen your Gmail security from any possible cyber threats.
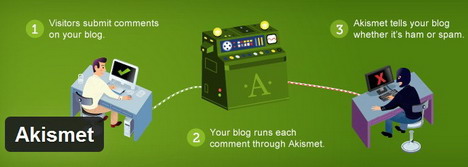
23 Best WordPress Anti Spam Plugins
Which is the best anti spam plugin for WordPress blog? WordPress is a very popular content management system that loads with various blogging security features, and that includes spam filtering. If you think that the built-in anti spam feature isn’t enough, and you’re looking for something more sophisticated. Below we’ve listed 23 anti spam plugins which can provide you extra features for effectively fighting spam on WordPress blog. We also recommend some useful captcha anti spam plugins for your consideration.
5 Useful Tips to Protect Online Account Passwords from Hacker
These days, hacking is becoming a real issue. As a regular Internet user, we should do our best to make sure our online accounts are safe. Having accounts hacked can be dangerous, If someone gains access to your online account they can do whatever they like. Just imagine that if the password of your online banking account falls into the hand of cyber criminal, all your savings will be gone in seconds. Certainly you will never want this happens in your life.
To prevent this online security threat, below are some useful tips to help you protect your passwords effectively. Don’t miss it! Read more…
30 Best Data Backup, Restore and Synchronization Software Programs
Which is the best backup software program? Well, every computer user should know how important data backup is because we never know when our computer goes down due to hardware failure or virus attack. Without having your data backed up, you are like putting your school assignments, memorable photos, or work projects at risk. All these important data could vanish in the next hour if your computer hard disk is suddenly corrupted.
To avoid the risk of losing your computer data, you should make it a habit to back up all your important files, document, photos, emails and work in progress on a regular basis. Below are 30 popular data backup, restore and synchronization tools for your computer hard disk and external storage devices. Most of these software programs are free for use, and they can help you backup your files in a more efficient and simple way! Read more…